Offline Cluster Scanning
Overview
nctl provides a seamless way to scan Kubernetes clusters for misconfigurations without the need for any in-cluster agents. Leveraging the kubeconfig and Kubernetes context, nctl scans your clusters against policysets defined in Nirmata. The results are then published in the NCH dashboard, where you can view detailed insights and remediation steps, share reports with your team, and manage multiple clusters from a single platform.
Key Features
- Agent-less scanning: No need to install agents in your Kubernetes clusters.
- Policy-based scanning: Automatically scans clusters against policysets defined in Nirmata.
- Real-time insights: Get immediate, actionable security and operational reports.
- Unified dashboard: View results for all clusters in one central platform.
Prerequisites
- Kubernetes Access: Ensure you have access to your clusters via kubectl and a valid kubeconfig file.
- Nirmata Account: You will need an active NCH account for policy management and report viewing. If you don’t have one, sign up for a 15-day free trial.
- Tools:
- nctl: Download the CLI tool here
- kubectl: Ensure kubectl is installed and configured
Setup and Configuration
Step 1: Verify Kubernetes Context
Before running any scan, ensure that you are using the correct Kubernetes context. To check your current context, run the following command:
kubectl config current-context
If you need to switch to a different context, use the command:
kubectl config use-context <your-cluster-context>
Step 2: Configure Policies for Scan
Policies can be loaded from various sources. The following options are available:
- Use the
--policiesflag to load policies from the local filesystem or point to a Git URL - Use the
--cluster-policiesflag if you want to use policies already present in the cluster - Use the
--policysetsflag to refer to policysets in NCH - If you are logged into NCH, the policysets that are marked as default or have matching label selectors will be used for scanning
- If none of the above apply, nctl uses three default policysets:
- Pod Security Standard - Baseline
- Pod Security Standard - Restricted
- RBAC Best Practices
Performing an Offline Scan
Step 1: Initiate the Scan
Once you’ve set up your policies, initiate the scan using nctl. The CLI will automatically detect the active Kubernetes context and scan your cluster against the configured policies.
Login to NCH to retrieve policysets and publish the results of the scan.
nctl login npm --url https://www.nirmata.io --userid <userid> --token <API_TOKEN>
Run the following command:
nctl scan kubernetes --cluster-resources --publish
Note: The reports will be published to NCH only if you are logged into your NCH account.
This command will:
- Scan the currently selected Kubernetes context.
- Report misconfigurations against the configured policies.
- Output the results directly to your CLI.
Step 2: View Results in the CLI
Once the scan is complete, the results are shown directly in your terminal. The output includes:
- A summary of passed and failed policy checks.
- Detailed information on violations.
Viewing and Managing Scan Reports in NCH
Step 1: Access the NCH Dashboard
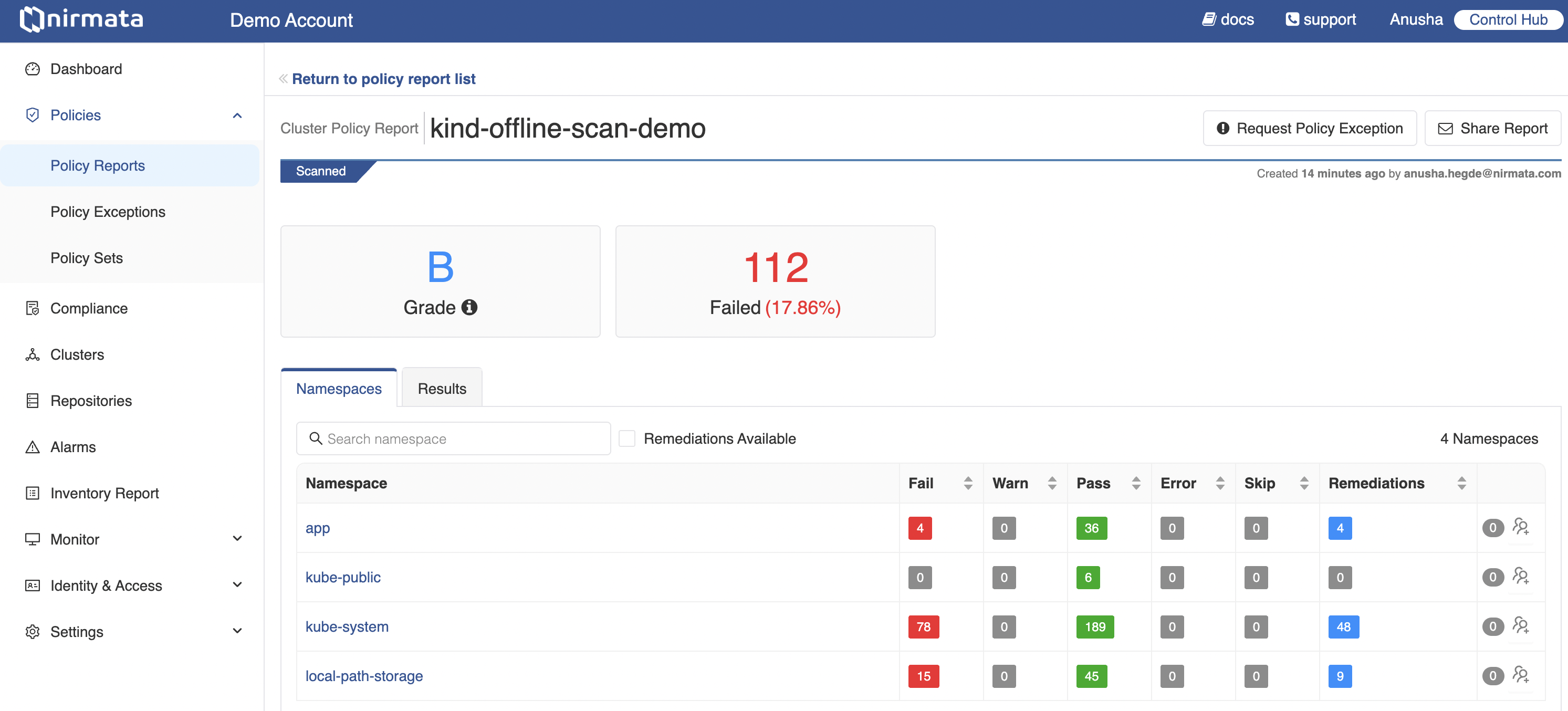
After scanning, the results are automatically published to the NCH dashboard, where you can see a unified view of your cluster scans.
- Login to the NCH Dashboard.
- Navigate to Cluster Reports: Go to the Policy Reports > Clusters section to view all scans across multiple clusters.
Step 2: Analyze and Share Results
The NCH dashboard provides detailed insights into each scan:
- Unified View: See the security posture of multiple clusters, with aggregated grades and detailed pass/fail results.
- Issue Breakdown: Dive into individual policy violations for more detailed information, including affected resources and remediation steps.
- Collaboration Features: Share reports with team members or export them for auditing purposes.
