Pipeline Scanning
Pipeline Scanning Workflow
nctl scan can be used within the local CLI environment; however, its true potential is unlocked when utilized within CI pipelines to scan code repositories.
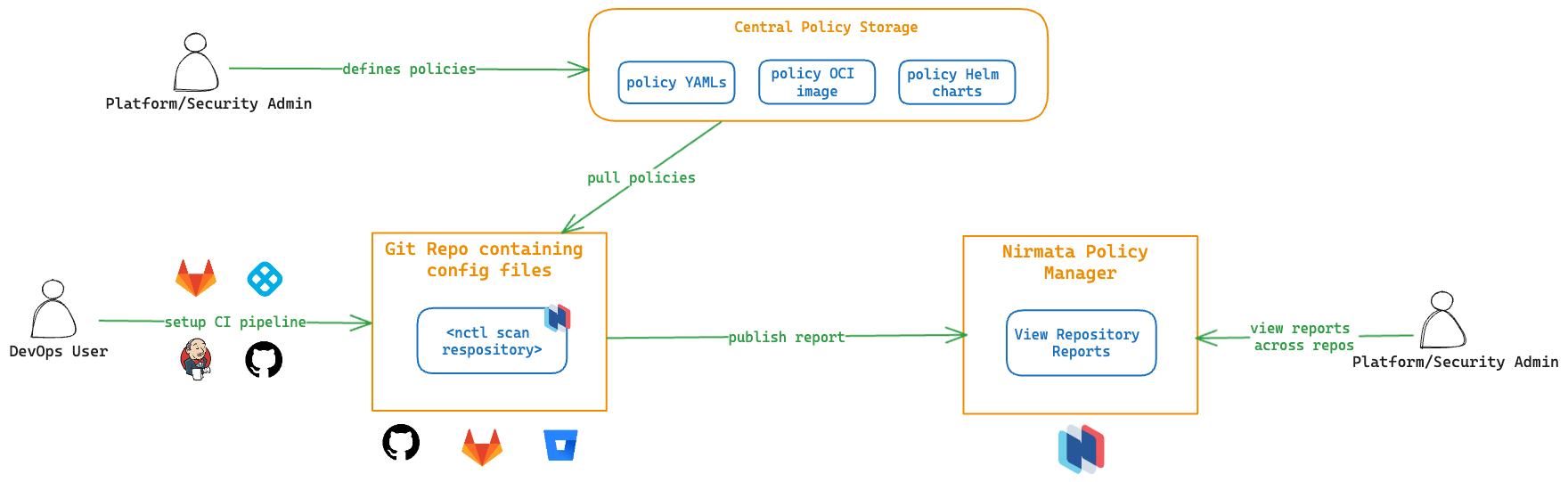
Platform or security team administrators are responsible for defining the policies that an organization needs to adhere to. These policies are stored as YAML files in Git repositories, as OCI images in the OCI registry, or are made available as Helm charts. The DevOps users or IT team is responsible for managing the configuration files, whether they are Kubernetes manifests, IaC files, or any JSON specs stored in Git repositories.
Users who want to make changes to the manifests in these repositories will create a pull request (PR). CI pipelines are configured to trigger on various actions, such as creating a PR, merging code to the main branch, or running at regular intervals.
Setting up the CI Pipeline
NCTL works with any CI pipeline (GitHub Action, GitLab CI, Jenkins, Harness CI, etc.).
