Remediations
NCH provides tailored remediation suggestions for policy violations to guide developers through the resolution process. This ensures that issues are addressed promptly and effectively, maintaining optimal system performance and security.
Remediation With Mutate Policy
By default, NCH provides remediation suggestions for all curated policysets - which include Pod Security Standards (Baseline and Restricted profiles) and RBAC Best Practices.
Remediation suggestions utilize the mutate capability of Kyverno. By following the policy annotation convention, NCH can display remediation suggestions for violations, even for custom policies.
- The annotation
policies.nirmata.io/remediation-docscan be used to link to an external webpage that contains detailed explanation of the policy violation. This can be a link on the internet, or internal wiki/docs links that guide developers with the resolution process. - The annotation
policies.nirmata.io/remediationshould contain a reference to a mutate Kyverno policy that is used for providing remediation suggestions. Below is an example of an annotation from a policy:
policies.nirmata.io/remediation-docs: "https://docs.nirmata.io/policysets/podsecurity/baseline/disallow-host-namespaces/"
policies.nirmata.io/remediation: "https://github.com/nirmata/kyverno-policies/tree/main/pod-security/baseline/disallow-host-namespaces/remediate-disallow-host-namespaces.yaml"
- NCH can then provide remediation suggestions based on the mutate policy.
Note: It is important to annotate a ClusterPolicy with its corresponding mutate policy for the NCH remediation feature to work as expected.
Testing Custom Remediations
To test custom remediations, use nctl to test the validity of the mutate policy. Ensure that the policy follows the annotation conventions mentioned above.
For example,
nctl remediate -p <path to policy file|dir> -r <path to resource>
Read more about the remediate command here.
Viewing Remediation Suggestions in NCH
To view Remediation Suggestions in Policy Reports:
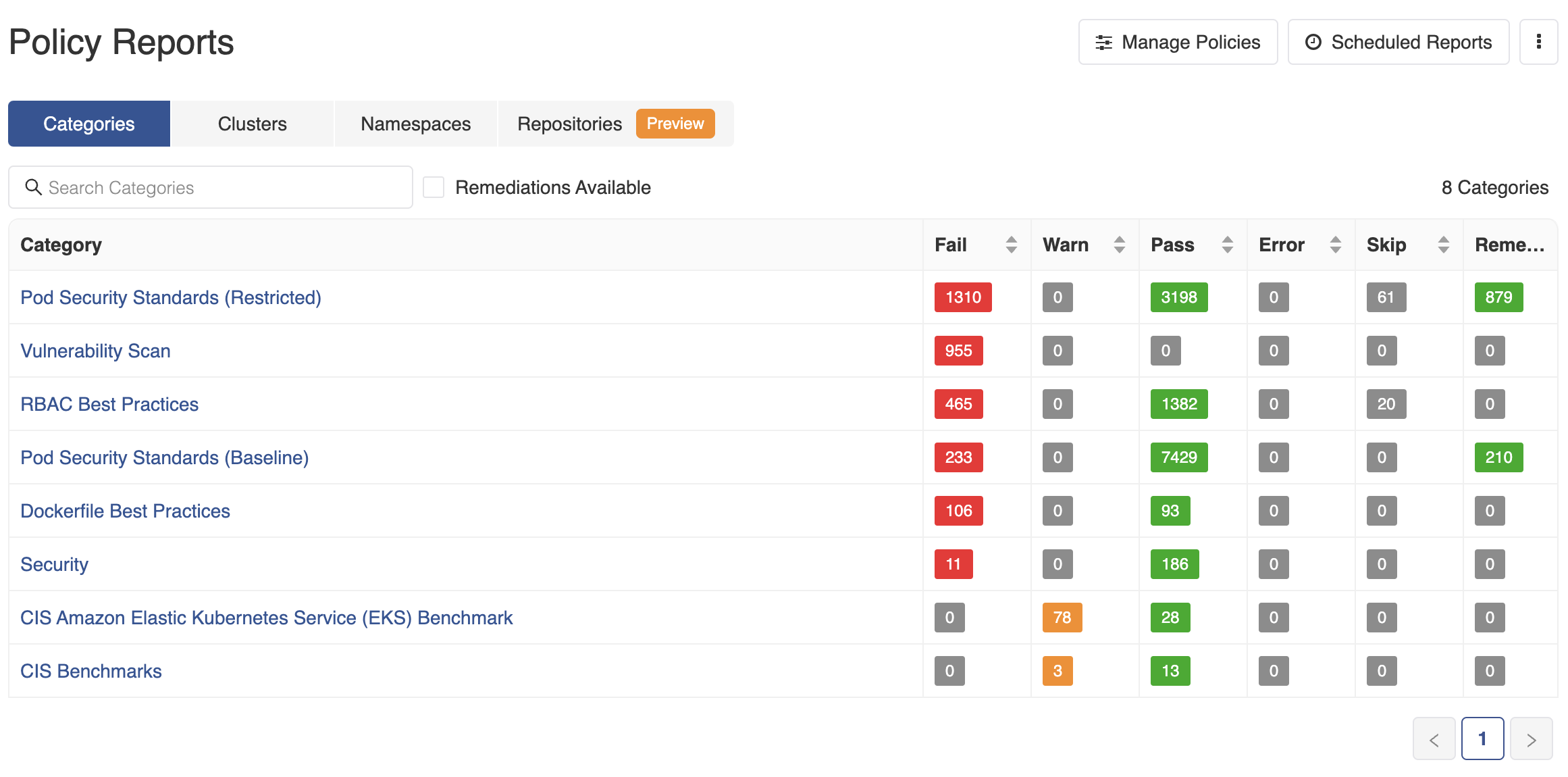
- Go to Policies>Policy Reports. The Policy Reports can be viewed based on collections such as Categories, Clusters, or Namespaces. Under each collection, there is a
Remediationcolumn that shows the number of remediations available for that category, cluster, or namespace. - Click on the Remediations Available button available beside the search bar to filter the list to only contain the rows that have remediations available.
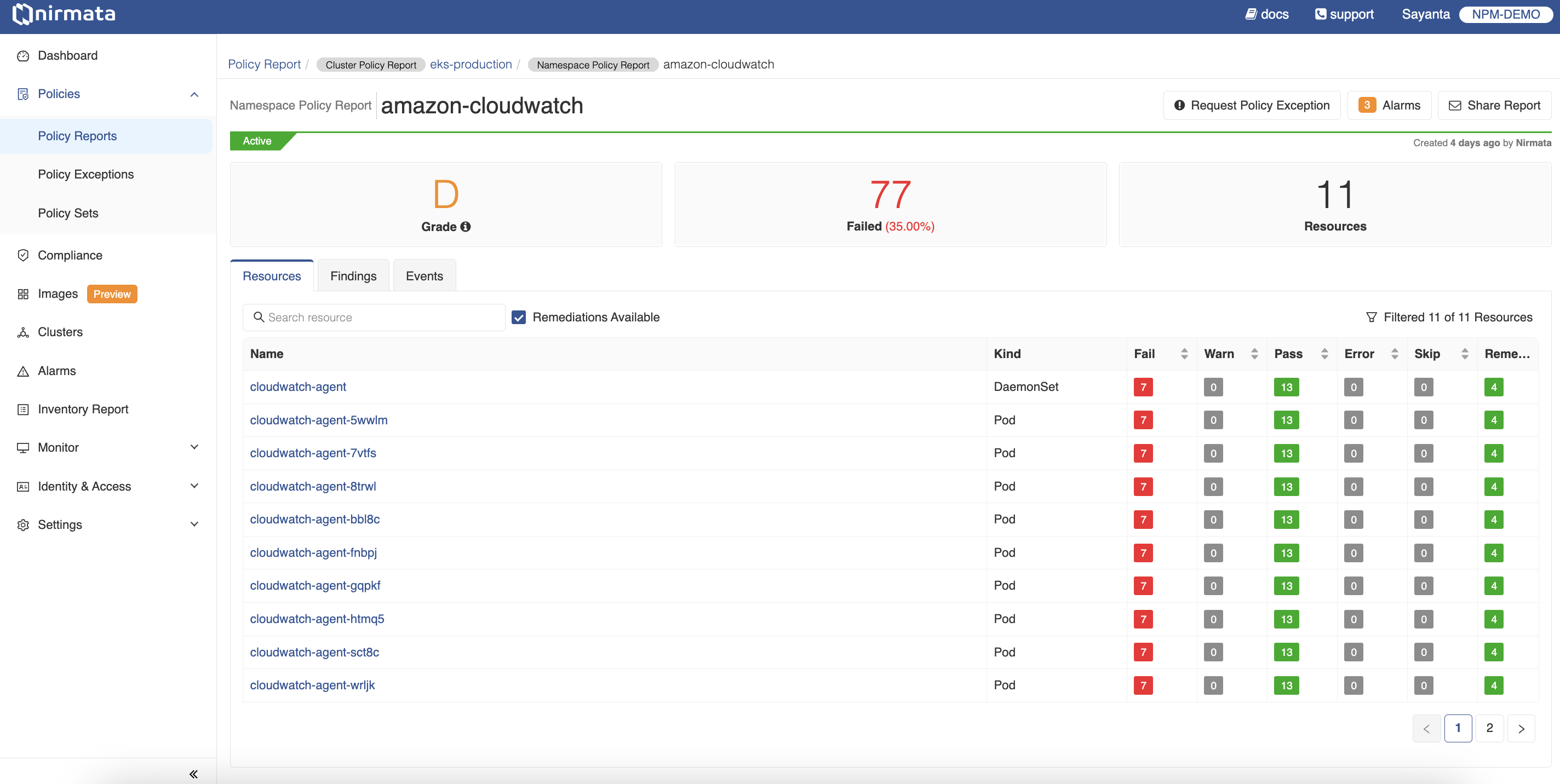
- Click on any of the Cluster Name (example, eks-production) link to view the list of namespaces containing policy reports that have remediations available.
- Click on any of the remediation-available namespaces to get the list of findings. Go to the Resources tab to find the list of impacted resources in the namespace and filter the ones with remediations available by checking the ‘Remediations Available’ button. The page also shows the namespace grade along with the total number of resources and violations associated with the resources.
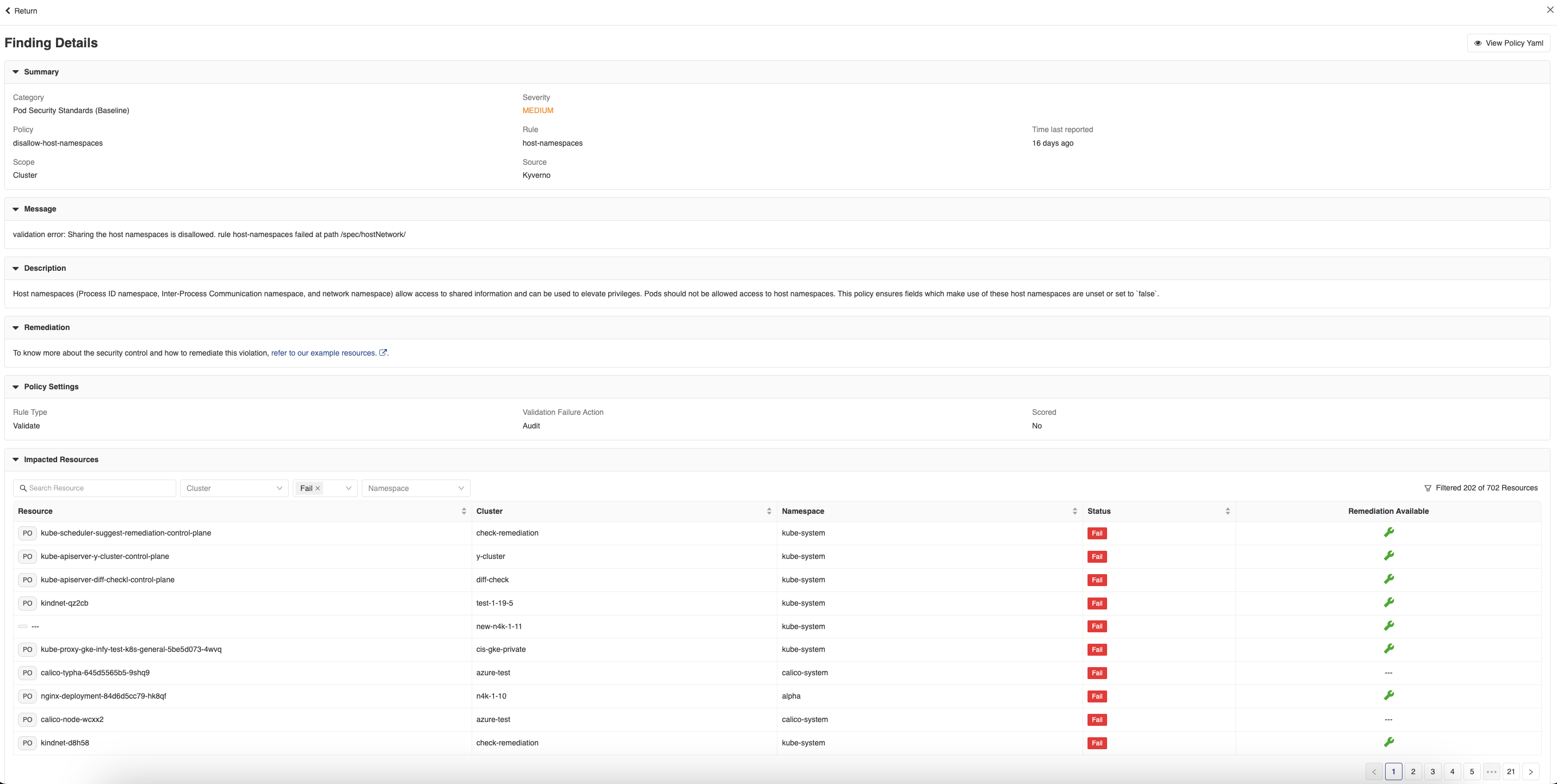
- Now, click on any of the impacted resources to view the findings related to that particular resource, their severity, status, and whether remediations are available for those findings. The page also summarizes the number of remediations available out of the violations, the namespace grade impact after the remediation is applied, and the number of affected child resources that can be fixed with the applied remediations.
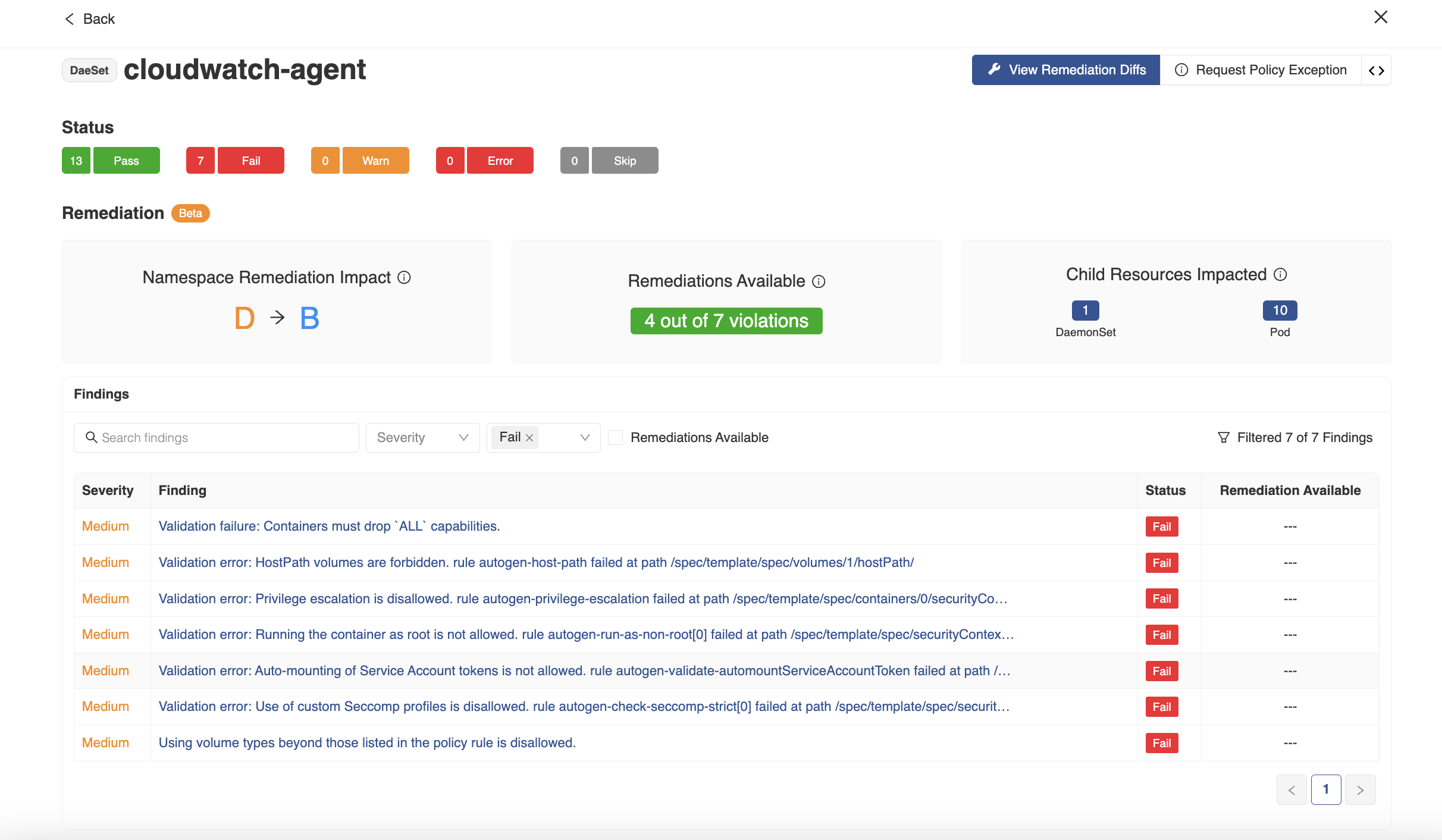
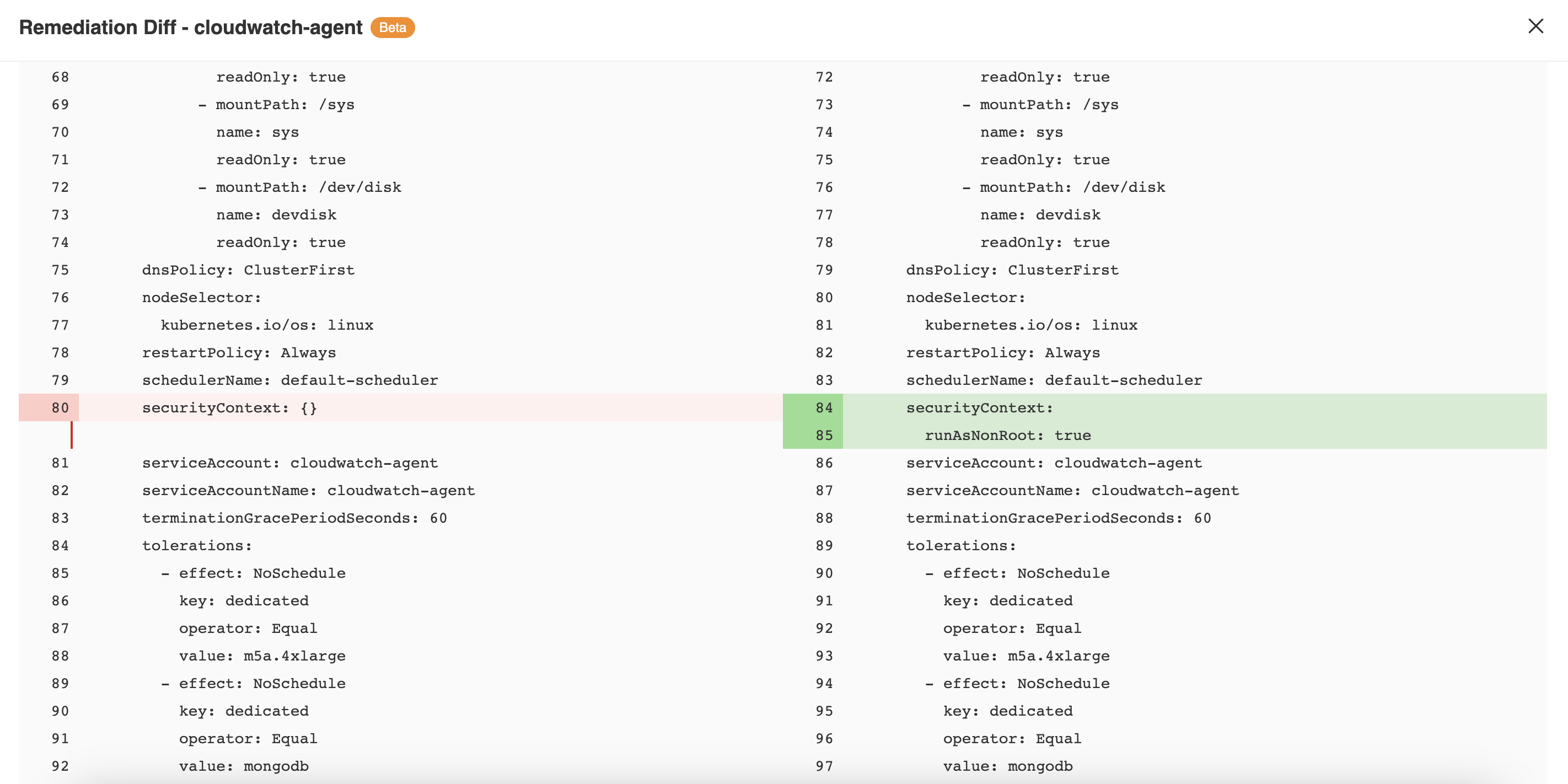
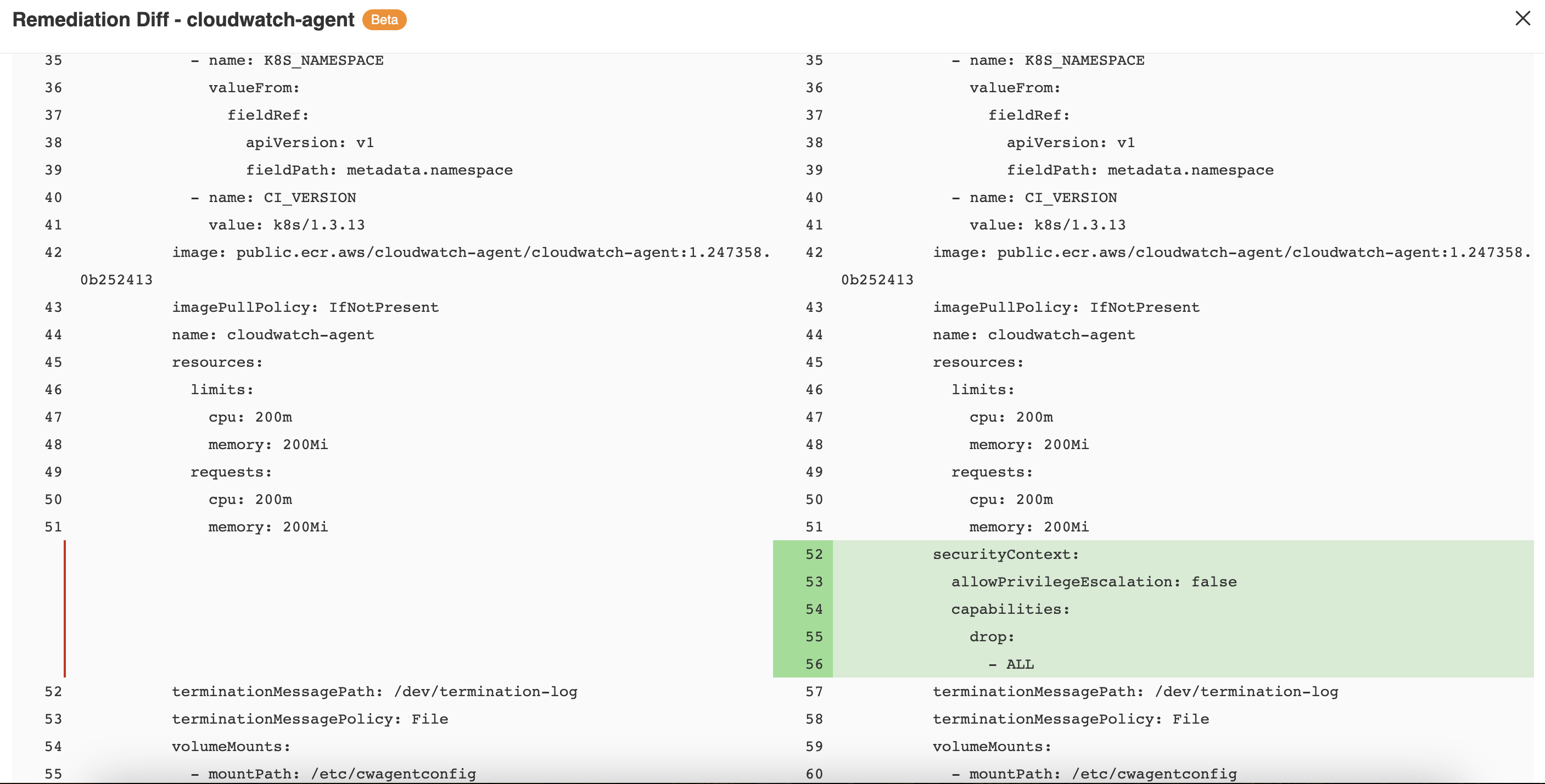
- Click on the View Remediation Diffs button located at the top right-hand section of the screen to get a side-by-side view of the resource YAML and the remediated resource YAML. Both of the resources YAML can be downloaded by clicking on the download button.
- Click on any of the findings link with remediation available to view the detailed report, the remediation suggestions, and the list of impacted resources.